SkyDog: 2016 - Catch Me If You Can
References
- https://www.vulnhub.com/entry/skydog-2016-catch-me-if-you-can,166/
- http://www.hackingarticles.in/hack-skydog-con-ctf-2016-catch-can-vm/
- https://www.jamesbower.com/skydog-con-2016-ctf/
重點工具與技巧
- 更改user-agent
- 隱碼工具:
steghide - windows記憶體鑑識工具:
volatility
Writeup
- Web:
http://10.0.2.133/index.html- 檢視原始碼
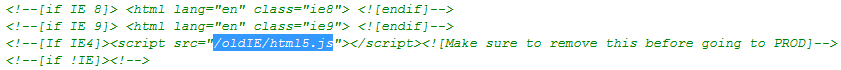
- 發現hex值

- 解碼後得到第一組flag:
"666c61677b37633031333230373061306566373164353432363633653964633166356465657d".decode("hex") 'flag{7c0132070a0ef71d542663e9dc1f5dee}' john --format=raw-md5 md5hash.txt後得到nmap
- 檢視原始碼
- 連上ssh 22222 port得到第二組flag:
sean@LinuXMint ~ $ ssh -p 22222 10.0.2.133 The authenticity of host '[10.0.2.133]:22222 ([10.0.2.133]:22222)' can't be established. ECDSA key fingerprint is SHA256:DeCMZ74o5wesBHFLyaVY7UTCA7mW+bx6WroHm6AgMqU. Are you sure you want to continue connecting (yes/no)? yes Warning: Permanently added '[10.0.2.133]:22222' (ECDSA) to the list of known hosts. ############################################################### # WARNING # # FBI - Authorized access only! # # Disconnect IMMEDIATELY if you are not an authorized user!!! # # All actions Will be monitored and recorded # # Flag{53c82eba31f6d416f331de9162ebe997} # ###############################################################- md5 crack後得到
encrypt
- md5 crack後得到
- 連到https://10.0.2.133 並檢查憑證
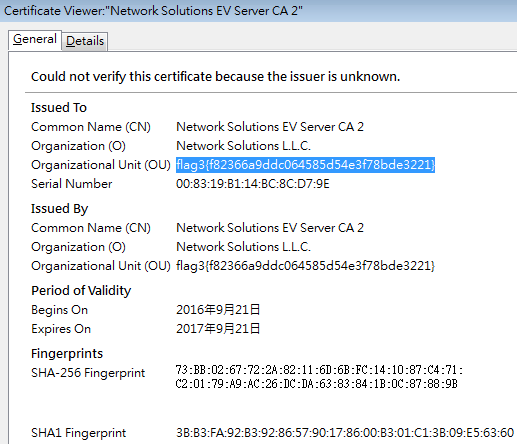
- 得到第三組flag,md5 crask後得到
personnel
- 得到第三組flag,md5 crask後得到
-
ACCESS DENIED!!! You Do Not Appear To Be Coming From An FBI Workstation. Preparing Interrogation Room 1. Car Batteries Charging....- 其中提到
FBI Workstation - 回到
http://10.0.2.133/oldIE/html5.js,發現:/* maindev - 6/7/02 Adding temporary support for IE4 FBI Workstations */ - 使用burp修改user-agent(https://www.nczonline.net/blog/2010/01/12/history-of-the-user-agent-string/)
改為User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:50.0) Gecko/20100101 Firefox/50.0User-Agent: Mozilla/5.0 (Windows NT 6.1; MSIE 4.0; rv:50.0) Gecko/20100101 Firefox/50.0 即可看見網頁內容,並發現第四組flag:
flag{14e10d570047667f904261e6d08f520f} Clue = new+flag- md5 crack為
evidence - 根據線索提示,
Clue應為newevidence
- md5 crack為
- 其中提到
- 連到http://10.0.2.133/newevidence ,同樣使用IE4.0 user-agent
- 接著會要求輸入帳號密碼登入,這時就要利用OSINT方法,有點運氣,通常就是搜集網頁或這部電影的相關資料,例如台詞等,再來暴破帳密,可使用工具
cewl - 最後使用帳號
carl.hanratty和密碼Grace來登入,發現有三個連結 - 其中在
http://10.0.2.133/newevidence/Evidence.txt發現第五組flag:flag{117c240d49f54096413dd64280399ea9},md5 crack後為panam
- 接著會要求輸入帳號密碼登入,這時就要利用OSINT方法,有點運氣,通常就是搜集網頁或這部電影的相關資料,例如台詞等,再來暴破帳密,可使用工具
- 在
http://10.0.2.133/newevidence/Invoice.pdf有個PDF,其中提到的姓名就是steghide隱碼工具的作者 在
http://10.0.2.133/newevidence/image.jpg發現圖片,因此可使用steghide來解看看steghide extract -sf image.jpg得到第六組flagflag{d1e5146b171928731385eb7ea38c37b8} =ILoveFrance clue=iheartbrenda
- 而第七組提示也是需要OSINT方法,電影有提到Barry Allen和線索最快的人,所以就想到閃電俠
- 最後就使用帳號
barryallen和先前的線索iheartbrenda當作密碼來登入ssh - 馬上就看到第七組flag:
flag{bd2f6a1d5242c962a05619c56fa47ba6},md5 crack後為theflash
- 最後就使用帳號
下載另一個檔案
security-system.data- 從內容猜測是memory image,使用
volatility分析看看root@kali:~/Downloads# volatility -f security-system.data imageinfo Volatility Foundation Volatility Framework 2.5 INFO : volatility.debug : Determining profile based on KDBG search... Suggested Profile(s) : WinXPSP2x86, WinXPSP3x86 (Instantiated with WinXPSP2x86) AS Layer1 : IA32PagedMemoryPae (Kernel AS) AS Layer2 : FileAddressSpace (/root/Downloads/security-system.data) PAE type : PAE DTB : 0x33e000L KDBG : 0x80545b60L Number of Processors : 1 Image Type (Service Pack) : 3 KPCR for CPU 0 : 0xffdff000L KUSER_SHARED_DATA : 0xffdf0000L Image date and time : 2016-10-10 22:00:50 UTC+0000 Image local date and time : 2016-10-10 18:00:50 -0400 接著將console的history取出來
root@kali:~/Downloads# volatility -f security-system.data --profile=WinXPSP2x86 consoles Volatility Foundation Volatility Framework 2.5 ConsoleProcess: csrss.exe Pid: 560 Console: 0x4f23b0 CommandHistorySize: 50 HistoryBufferCount: 1 HistoryBufferMax: 4 OriginalTitle: %SystemRoot%\system32\cmd.exe Title: C:\WINDOWS\system32\cmd.exe AttachedProcess: cmd.exe Pid: 1336 Handle: 0x2d4 CommandHistory: 0x10186f8 Application: cmd.exe Flags: Allocated, Reset CommandCount: 2 LastAdded: 1 LastDisplayed: 1 FirstCommand: 0 CommandCountMax: 50 ProcessHandle: 0x2d4 Cmd #0 at 0x1024400: cd Desktop Cmd #1 at 0x4f2660: echo 66 6c 61 67 7b 38 34 31 64 64 33 64 62 32 39 62 30 66 62 62 64 38 39 63 37 62 35 62 65 37 36 38 63 64 63 38 31 7d > code.txt Screen 0x4f2ab0 X:80 Y:300 Dump: Microsoft Windows XP [Version 5.1.2600] (C) Copyright 1985-2001 Microsoft Corp. C:\Documents and Settings\test>cd Desktop C:\Documents and Settings\test\Desktop>echo 66 6c 61 67 7b 38 34 31 64 64 33 64 62 32 39 62 30 66 62 62 64 38 39 63 37 62 35 62 65 37 36 38 63 64 63 38 31 7d > code.txt C:\Documents and Settings\test\Desktop> ConsoleProcess: csrss.exe Pid: 560 Console: 0x1028488 CommandHistorySize: 50 HistoryBufferCount: 2 HistoryBufferMax: 4 OriginalTitle: ?OystemRoot%\system32\cmd.exe Title:- 發現有hex值寫入code.txt,解碼後得到最後一組flag:
flag{841dd3db29b0fbbd89c7b5be768cdc81},md5 crack為Twolittlemice
- 從內容猜測是memory image,使用