7.7 Sniffing Tools
Sniffing Tool: Wireshark
- It lets you capture and interactively browse the traffic running on a computer network.
- Wireshark uses Winpcap to capture packets, so it can only capture the packets on the networks supported by Winpcap.
- It captures live network traffic from Ethernet, IEEE 802.11, PPP/HDLC, ATM, Bluetooth, USB, Token Ring, Frame Relay, FDDI networks.
- Captured files can be programmatically edited via command-line.
- A set of filters for customized data display can be refined using a display filter.
Follow TCP Stream in Wireshark
- The tool sees TCP data in the same way as that of the application layer. Use this tool to find passwords in a Telnet session or make sense of a data stream.
Display Filters in Wireshark (重要)
- Display filters are used to change the view of packets in the captured files.
- Display Filtering by Protocol:
- Example: Type the protocol in the filter box; arp, http, tcp, udp, dns, ip
- Monitoring the Specific Ports:
tcp.port==23ip.addr==192.168.1.100 machine ip.addr==192.168.1.100 && tcp.port=23
- Filtering by Multiple IP Addresses:
ip.addr==10.0.0.4 or ip.addr==10.0.0.5
- Filtering by IP Address:
ip.addr==10.0.0.4
- Other Filters:
ip.dst==10.0.1.50 && frame.pkt_len>400ip.addr==10.0.1.12 && icmp && frame.number > 15 && frame.number < 30ip.src==205.153.63.30 or ip.dst==205.153.63.30
Additional Wireshark Filters
- Displays all TCP resets:
tcp.flags.reset==1
- Set a filter for the HEX values of 0x33 0x27 0x58 at any offset:
udp contains 33:27:58
- Displays all HTTP GET requests:
http.request
- Displays all retransmissions in the trace:
tcp.analysis.retransmission
- Displays all TCP packets that contain the word 'traffic':
tcp contains traffic
- Masks out arp, icmp, dns, or other protocols and allows you to view traffic of you interest:
!(arp or icmp or dns)
Sniffing Tool: StellCentral Packet Analyzer
- StellCentral Packet Analyzer provides a graphical console for high-speed packet analysis.
Sniffing Tool: Tcpdump/Windump (重要)
- TCPdump is a command line interface packet sniffer which runs on Linux and Windows.
- TCPDump: Runs on Linux and UNIX systems (重要)
- WinDump: Runs on Windows systems
Packet Sniffing Tool: Capsa Network Analyzer
- Capsa Network Analyzer captures all data transmitted over the network and provides a wide range of analysis statistics in an intuitive and graphic way.
Network Packet Analyzer: OmniPeek Network Analyzer
- OmniPeek sniffer displays a Google Map in the OmniPeek capture window showing the locations of all the public IP addresses of captured packets.
- This feature is a great way to monitor the network in real time, and show from where in the world that traffic is coming.
Network Packet Analyzer: Observer
- Observer provides a comprehensive drill-down into network traffic and provides back-in-time analysis, reporting, trending, alarms, application tools, and route monitoring capabilities.
Network Packet Analyzer: Sniff-O-Matic
- Sniff-O-Matic is a network protocol analyzer and packet sniffer that captures network traffic and enables you to analyze the data.
TCP/IP Packet Crafter: Colasoft Packet Builder
- Colasoft Packet Builder allows user to select one from the provided templates: Ethernet Packet, ARP Packet, IP Packet, TCP Packet and UDP Packet, and change the parameters in the decoder editor, hexadecimal editor, or ASCII editor to create a packet.
Network Packet Analyzer: RSA NetWitness Investigator
- RSA NetWitness Investigator captures live traffic and process packet files from virtually any existing network collection devices.
Additional Sniffing Tools
Packet Sniffing Tools for Mobile: Wi.cap. Network Sniffer Pro and FaceNiff
- Wi.cap. Network Sniffer Pro: Mobile network packet sniffer for ROOT ARM droids.
- FaceNiff: FaceNiff is an Android app that allows you to sniff and intercept web session profiles over the Wi-Fi.
Q1) You want to capture Facebook website traffic in Wireshark. What display filter should you use that shows all TCP packets that contain the word 'facebook'?
- display==facebook
- traffic.content==facebook
- tcp contains facebook
- list.display.facebook
A1) The appropriate Wireshark display filter is the following: tcp contains search-string.
Q2) NTP allows you to set the clocks on your systems very accurately, to within 100ms and sometimes-even 10ms. Knowing the exact time is extremely important for enterprise security. Various security protocols depend on an accurate source of time information in order to prevent "playback" attacks. These protocols tag their communications with the current time, to prevent attackers from replaying the same communications, e.g., a login/password interaction or even an entire communication, at a later date. One can circumvent this tagging, if the clock can be set back to the time the communication was recorded. An attacker attempts to try corrupting the clocks on devices on your network. You run Wireshark to detect the NTP traffic to see if there are any irregularities on the network. What port number you should enable in Wireshark display filter to view NTP packets?
- TCP Port 124
- UDP Port 125
- UDP Port 123
- TCP Port 126
A2) The appropriate port for NTP is UDP 123.
Q3) Which of the following problems can be solved by using Wireshark?
- Tracking version changes of source code
- Checking creation dates on all webpages on a server
- Resetting the administrator password on multiple systems
- Troubleshooting communication resets between two systems
Q4) Which technical characteristic do Ethereal/Wireshark, TCPDump, and Snort have in common?
- They are written in Java.
- They send alerts to security monitors.
- They use the same packet analysis engine.
- They use the same packet capture utility.
Q5) Which of the following is a command line packet analyzer similar to GUI-based Wireshark?
- Jack the ripper
- nessus
- tcpdump
- ethereal
Q6) The network administrator contacts you and tells you that she noticed the temperature on the internal wireless router increases by more than 20% during weekend hours when the office was closed. She asks you to investigate the issue because she is busy dealing with a big conference and she doesn’t have time to perform the task. What tool can you use to view the network traffic being sent and received by the wireless router?
- Netcat
- Wireshark
- Nessus
- Netstat
Q7) Which of the following tools is used to analyze the files produced by several packet-capture programs such as tcpdump, WinDump, Wireshark,and EtherPeek?
- Nessus
- Tcptraceroute
- Tcptrace
- OpenVAS
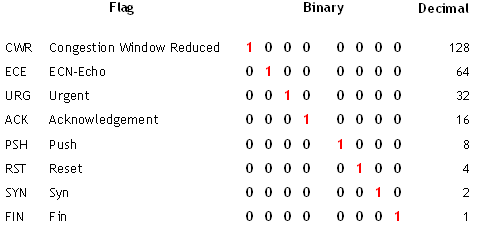
Q8) A pen tester configures this filter on a Wireshark capture: tcp.flags == 0x18. What TCP flags are being filtered on?
- SYN
- ACK
- SYN + ACK
- None of the above (但題目是0x18 這是16進制,轉十進制是24=16+8=ACK+PSH,所以答案應該是4,不然就是題目寫錯了,「tcp.flags == 18」才對)
A8) Wireshark can make use of decimal values assigned to TCP flags; 18 equates to ACK (16) and SYN (2).
Q9) You are reviewing a packet capture in Wireshark but only need to see packets from IP address 198.162.15.17. Which of the following filters will provide the output you want to see?
- ip == 198.162.15.17
- ip.address == 198.162.15.17
- ip.src == 198.162.15.17
- ip.source.address == 198.162.15.17
A9) ip.src == IPaddress will display only those packets with the specified source IP address.
- 補充:若要filter掉某個IP,要使用
!(ip.addr == 1.2.3.4),不能使用ip.addr != 1.2.3.4- A common mistake: https://www.wireshark.org/docs/wsug_html_chunked/ChWorkBuildDisplayFilterSection.html
Q10) A pen tester is configuring a Windows laptop for a test. In setting up Wireshark, what driver and library are required to allow the NIC to work in promiscuous mode?
- libpcap
- winprom
- winpcap
- promsw
Q11) Which command launches a CLI version of Wireshark?
- Wireshk
- dumpcap
- tshark
- editcap
A11) The command for the CLI version of Wireshark is tshark.
Q12) What is the generic syntax of a Wireshark filter?
- protocol.field operator value
- field.protocol operator value
- operator.protocol value field
- protocol.operator value field
A12) Wireshark filters use the basic syntax of putting the protocol first followed by the field of interest, the operator to be used, and finally the value to look for (tcp.port == 23).
Q13) Wireshark requires a network card to be able to enter which mode to sniff all network traffic?
- Capture mode
- Promiscuous mode
- pcap mode
- Gather mode
A13) To sniff all traffic on a network segment promiscuous mode is required which allows all network traffic to be captured.
Q14) The command-line equivalent of Windump is known as?
- Wireshark
- TCPdump
- Windump
- Netstat
A14) TCPdump is a command line equivalent of windump which allows the sniffing of network traffic.
Q15) Which of the following software tools can perform sniffing? (Choose all that apply.)
- Dsniff
- Wireshark
- NetBSD
- Netcraft
A15) Dsniff and Wireshark are sniffer software tools.
Q16) What is the proper Wireshark filter to capture traffic only sent from IP address 131.1.4.7?
- ip.src == 131.1.4.7
- ip.address.src == 131.1.4.7
- ip.source.address == 131.1.4.7
- src.ip == 131.1.4.7
A16) ip.src == 131.1.4.7 will capture traffic sent from IP address 131.1.4.7.
Q17) Which Wireshark filter will only capture traffic to www.google.com?
- ip.dst = www.google.com
- ip.dst eq www.google.com
- ip.dst == www.google.com (這題有問題,四個指令都不對,正確應該是
http.host == www.google.com) - http.dst == www.google.com
Q18) Wireshark was previously known as _.
- Packet Sniffer
- Ethereal
- EtherPeek
- SniffIT
A18) Wireshark was previously called Ethereal.
Q19) Jason is the security administrator of ASPEN Communications. He analyzes some traffic using Wireshark and has enabled the following filters.
((tcp.flags == 0x02) || (tcp.flags == 0x12)) || ((tcp.flags == 0x10) && (tcp.ack==1) && (tcp.len==0))
- SYN,FIN,URG and PSH
- SYN,SYN/ACK,ACK
- RST,PSH/URG,FIN
- ACK,ACK,SYN,URG
A19)
- tcp.flags == 0x02: SYN
- tcp.flags == 0x12: decimal=18=2+16=SYN+ACK
- tcp.flags == 0x10: decimal=16=ACK
- tcp.ack==1: ack seq=1
- tcp.len==0: tcp length=0
Q20) When using Wireshark to acquire packet capture on a network, which device would enable the capture of all traffic on the wire?
A. Network tap B. Layer 3 switch C. Network bridge D. Application firewall
A20) Network tap: Any kind of connection that allows you to see all traffic passing by. Generally used in reference to a network-based IDS (NIDS) to monitor all traffic.
Q21) What is the command used to create a binary log file using tcpdump?
- tcpdump -w ./log
- tcpdump -r log
- tcpdump -vde logtcpdump -vde ? log
- tcpdump -l /var/log/
Q22) You are trying to hijack a telnet session from a victim machine with IP address 10.0.0.5 to Cisco router at 10.0.0.1. You sniff the traffic and attempt to predict the sequence and acknowledgement numbers to successfully hijack the telnet session.
Here is the captured data in tcpdump.
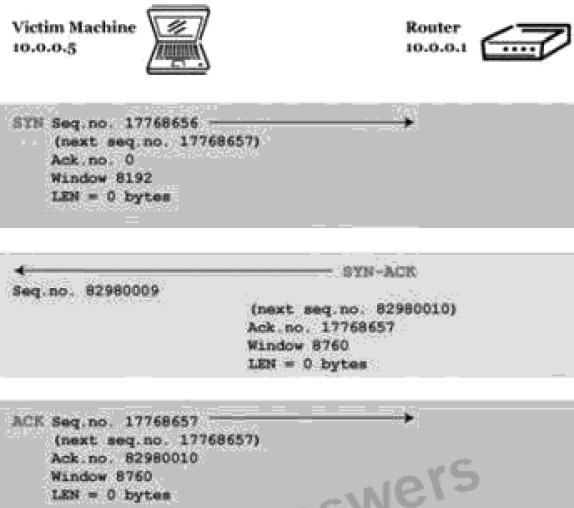

- Sequence number: 82980070 Acknowledgement number: 17768885A.
- Sequence number: 17768729 Acknowledgement number: 82980070B.
- Sequence number: 87000070 Acknowledgement number: 85320085C.
- Sequence number: 82980010 Acknowledgement number: 17768885D.
Q23) Windump is the windows port of the famous TCPDump packet sniffer available on a variety of platforms. In order to use this tool on the Windows platform you must install a packet capture library.
What is the name of this library?
- NTPCAP
- LibPCAP
- WinPCAP
- PCAP
A23) WinPcap is the industry-standard tool for link-layer network access in Windows environments: it allows applications to capture and transmit network packets bypassing the protocol stack,and has additional useful features,including kernel-level packet filtering,a network statistics engine and support for remote packet capture.
Q24) WinDump is a popular sniffer which results from the porting to Windows of TcpDump for Linux. What library does it use?
- LibPcap
- WinPcap
- Wincap
- None of the above
Q25) Jason is using TCPdump to capture traffic on his network. He would like to save the capture for later review. What command can Jason use?
- tcpdump −r capture.log
- tcpdump −l capture.log
- tcpdump −t capture.log
- tcpdump −w capture.log
A25) TCPdump uses the option –w to write a capture to a log file for later review. The option –r is used to read the capture file, or the capture can be opened in a GUI-based sniffer such as Wireshark.
Q26) Jason is using TCPdump to capture traffic on his network. He would like to review a capture log gathered previously. What command can Jason use?
- tcpdump −r capture.log
- tcpdump −l capture.log
- tcpdump −t capture.log
- tcpdump −w capture.log
A26) The option −r is used to read the capture file, or the capture can be opened in a GUI-based sniffer such as Wireshark.