11.4 Webserver Attack Tools
Webserver Attack Tool: Metasploit (重要)
- The Metasploit Framework is a penetration testing toolkit, exploit development platform, and research tool that includes hundreds of working remote exploits for a variety of platforms.
- It supports fully automated exploitation of web servers, by abusing known vulnerabilities and leveraging weak passwords via Telnet, SSH, HTTP, and SNM.
- 基本題會考
- Autopwn
Metasploit Architecture

The framework was designed to be as modular as possible in order to encourage the reuse of code across various projects.
Metasploit Exploit Module
- It is the basic module in Metasploit used to encapsulate an exploit using which users target many platforms with a single exploit.
- This module comes with simplified meta-information fields.
- Using a Mixins feature, users can also modify exploit behavior dynamically, brute force attacks, and attempt passive exploits.
- Steps to exploit a system follow the Metasploit Framework:
- Configuring Active Exploit
- Verifying the Exploit Options
- Selecting a Target
- Selecting the Payload
- Launching the Exploit
滲透攻擊模組 → 裡面有許多漏洞攻擊程式。
Metasploit Payload Module
- Payload module establishes a communication channel between the Metasploit framework and the victim host.
- It combines the arbitrary code that is executed as the result of an exploit succeeding.
- To generate payloads, first select a payload using the command:
- msf >
use windows/shell_reverse_tcp - msf payload(shell_reverse_tcp) >
generate -h
- msf >
- There are three types of payload modules provides by the Metasploit:
- Singles: It is self-contained and completely standalone.
- Stagers: It sets up a network connection between the attacker and victim.
- Stages: It is downloaded by stagers modules.
當滲透攻擊成功後將目標主機植入程式,目的在於取得該主機的使用權。
Metasploit Auxiliary Module
- Metasploit's auxiliary modules can be used to perform arbitrary, one-off actions such as port scanning, denial of service, and even fuzzing.
- To run auxiliary module, either use the
runcommand, or use theexploitcommand.
輔助模組 → 掃描、密碼猜測、敏感資訊探測、DOS。
Metasploit NOPS Moduel
- NOP modules generate a no-operation instructions used for blocking out buffers.
- Use
generatecommand to generate a NOP sled of an arbitrary size and display it in a given format OPTIONS:- -b < opt>: The list of characters to avoid: '\x00\xff'
- -h: Help banner
- -s < opt>: The comma separated list of registers to save
- -t < opt>: The output type: ruby, perl, c, or raw msf nop(opty2)>

- 空指令 → 也就是 No Operation,作用是讓目標系統在一個時間週期內,不執行任何的處理程序以提升攻擊者執行 exploit 成功的機率。
- POST Module: 目標攻擊成功後所提供的功能,例如,鍵盤側錄、權限提升等。
- Encoders Module: 加密模組 → 將Payload的程式進行加密以避免被防毒軟體發現。
Webserver Attack Tool: Wfetch
- WFetch allows attacker to fully customize an HTTP request and send it to a Web server to see the raw HTTP request and response data.
- It allows attacker to test the performance of Web sites that contain new elements such as Active Server Pages (ASP) or wireless protocols.
Web Password Cracking Tools: THC-Hydra and Brutus
- THC-Hydra:
- Hydra is a parallized login cracker which supports numerous protocols to attack.
- Brutus:
- It includes a multi-stage authentication engine and can make 60 simultaneous target connections.
- It supports no user name, single user name, multiple user name, password list, combo (user/password) list and configurable brute force modes.
Q1) A pentester is using Metasploit to exploit an FTP server and pivot to a LAN. How will the pentester pivot using Metasploit? (?)
- Issue the pivot exploit and set the meterpreter.
- Reconfigure the network settings in the meterpreter.
- Set the payload to propagate through the meterpreter.
- Create a route statement in the meterpreter.
Q2) Finding tools to run dictionary and brute forcing attacks against FTP and Web servers is an easy task for hackers. They use tools such as arhontus or brutus to break into remote servers.
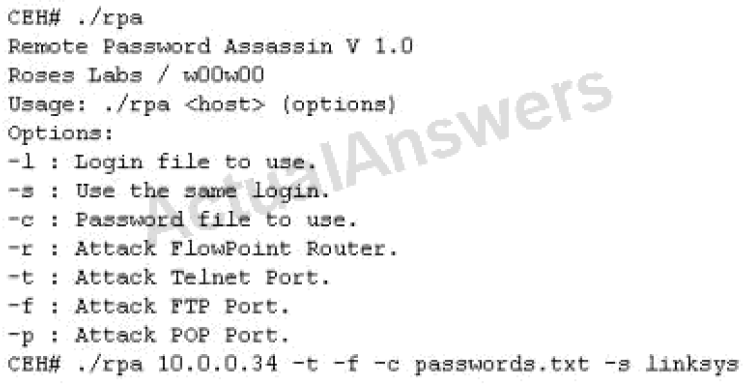
A command such as this, will attack a given 10.0.0.34 FTP and Telnet servers simultaneously with a list of passwords and a single login name. linksys. Many FTP-specific password-guessing tools are also available from major security sites.
What defensive measures will you take to protect your network from these attacks?
- Never leave a default password
- Never use a password that can be found in a dictionary
- Never use a password related to your hobbies,pets,relatives,or date of birth
- Use a word that has more than 21 characters from a dictionary as the password
- Never use a password related to the hostname,domain name,or anything else that can be found with whois