9.3 Botnets
Organized Cyber Crime: Organizational Chart
Botnet
- Bots are software applications that run automated tasks over the Internet and perform simple repetitive tasks, such as web spidering and search engine indexing.
- A botnet is a huge network of the compromised systems and can be used by an attacker to launch denial-of-service attacks.
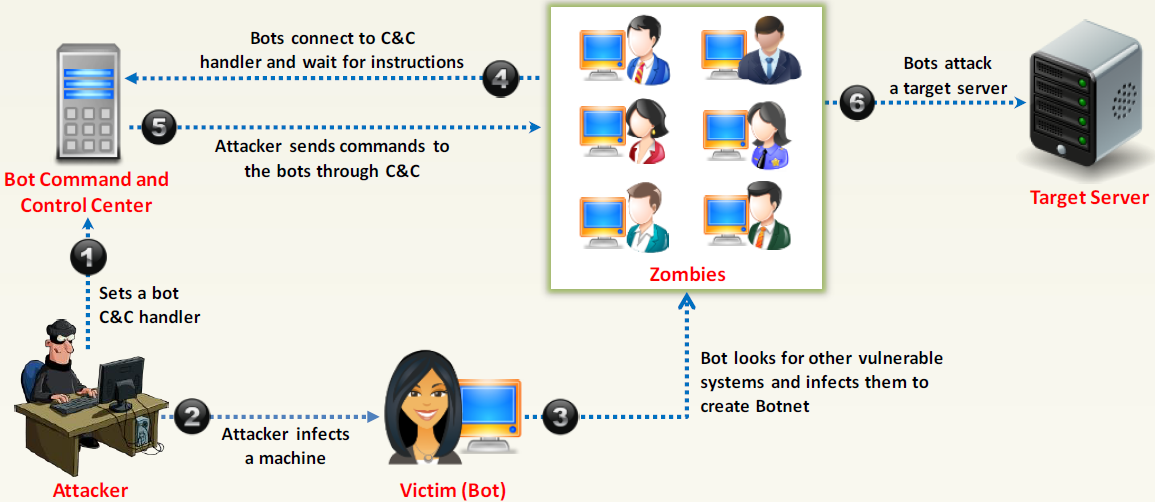
A Typical Botnet Setup

Botnet Ecosystem
Scanning Methods for Finding Vulnerable Machines
- Random Scanning: The infected machine probes IP addresses randomly from target network IP range and checks for the vulnerability.
- Hit-list Scanning: Attacker first collects list of possible potentially vulnerable machines and then perform scanning to find vulnerable machine.
基於一份潛在弱點攻擊目標清單,進行攻擊和傳播,被感染的主機再繼續傳播
- Topological Scanning: It uses the information obtained on infected machine to find new vulnerable machines.
根據被感染的主機搜集到的資訊,找出其它有弱點的主機,準確度較高
- Local Subnet Scanning: The infected machine looks for the new vulnerable machine in its own local network.
從受感染主機的本地子網路找尋其它有弱點的主機
- Permutation Scanning: It uses pseudorandom permutation list of IP addresses to find new vulnerable machines.
Divide and conquer
How Malicious Code Propagates?
- Attackers use three techniques to propagate malicious code to newly discovered vulnerable system:
- Central Source Propagation: Attacker places attack toolkit on the central source and copy of the attack toolkit is transferred to the newly discovered vulnerable system.
透過central source下載attack toolkit
- Back-chaining Propagation: Attacker places attack toolkit on his/her system itself and copy of the attack toolkit is transferred to the newly discovered vulnerable system.
需要時再從attacker中請求下載attack toolkit
- Autonomous Propagation: Attack toolkit is transferred at the time when the new vulnerable system is discovered.
Attacker在攻擊成功時就一起連attack toolkit載下來
- Central Source Propagation: Attacker places attack toolkit on the central source and copy of the attack toolkit is transferred to the newly discovered vulnerable system.
Botnet Trojan: Blackshades NET
- Blackshades NET has the ability to create implant binaries which employ custom obfuscation algorithms or Crypters, which can be bought through the Bot/Crypter marketplace embedded in the BlackShades controller.
Botnet Trojans: Cythosia Botnet and Andromeda Bot
Botnet Trojan: PlugBot
- PlugBot is a hardware botnet project.
- It is a covert penetration testing device (bot) designed for covert use during physical penetration tests.